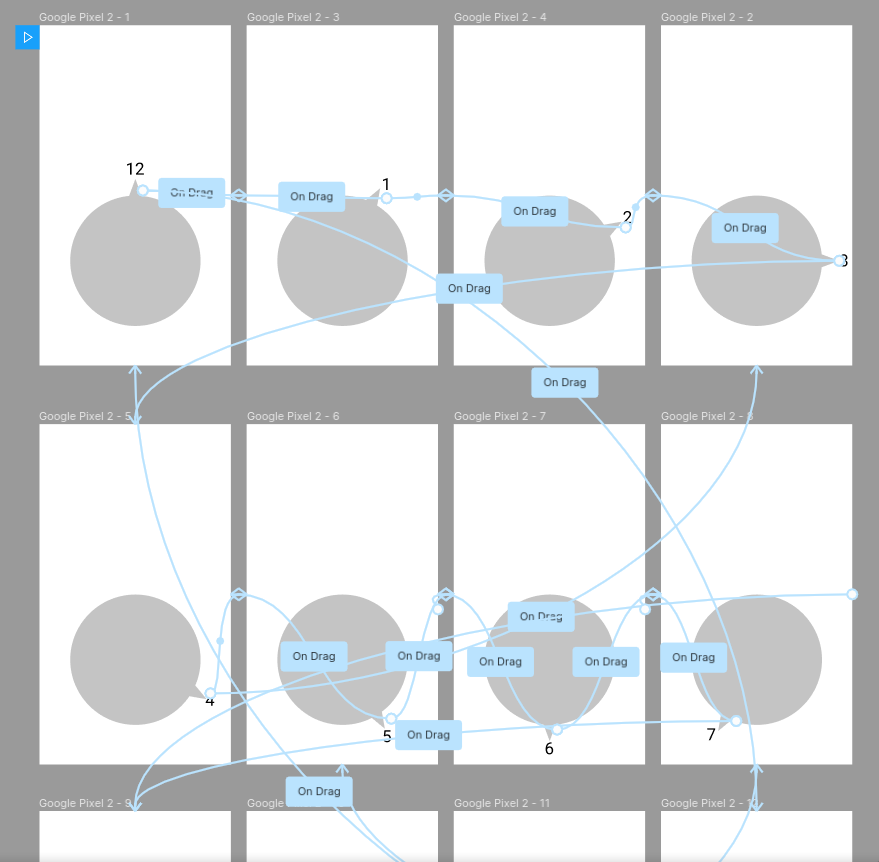
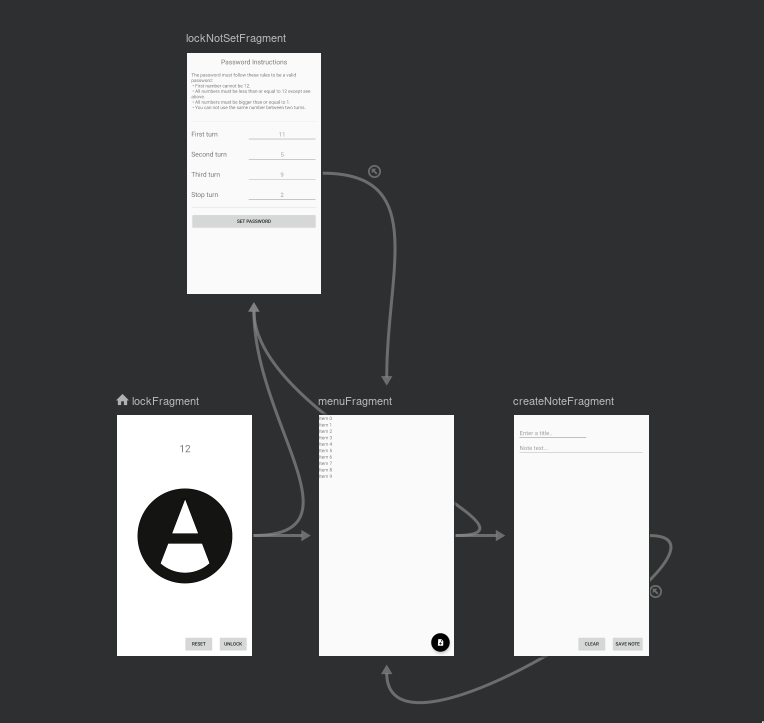
Empirical research was done before the development of VaultLock with the help of our prototypes. Our observational study was done with our digital prototype and the participation/empathy study was done with our native prototype.
Observations
Question to be answered: Is VaultLock desirable?
5 participants, 3 Follow-up questions at the end
Using observation technique to investigate desirability among potential users, the participants were asked to use the prototype and fill in a made up password, which was repeated with three different passwords, to let them get used to the idea. After the experiment, the participants were asked questions related to ease of use, practicality and whether they could see themselves using it or not.
Results
This showed us that the idea was desirable and was a precursor before development of VaultLock. The big factor that was important according to our users was to implement haptic feedback for each turn of the knob, which we brought with us in development.
Participation/Empathy
Question to be answered: Does it help against shoulder surfing?
2 participants
Using participation/empathy technique to investigate the viability of fighting shoulder surfing. Each participant got to be both the shoulder surfer and the victim with both of the unlocking mechanisms that was investigated (regular pin-code and the VaultLock). Each locking mechanism was used 5 times by each person.
Results
Regular pin-code replicated 7/10 times. Vault lock replicated 5/10 times.
Obviously more research is nescessary due to the limited amount of time to do this research and due to the limited number of participants for the study. But we can preliminary point and say that it seems to be safer than the ordinary pin-code. However it might be because of the novelty of VaultLock and not that it is safer in practicality.